We look at
CYBER
SECURITY
from a
DEVELOPMENT
PERSPECTIVE
Many security teams will start with infrastructure and networks.
Probing to see how a bad actor can get in to vour platform.
Our take is a bit different.
We think you're just as likely to be exposed by poor software - either in how it was built or is being maintained.
That open door in your software might be easier to slip through than dropping ninja style into your data centre.
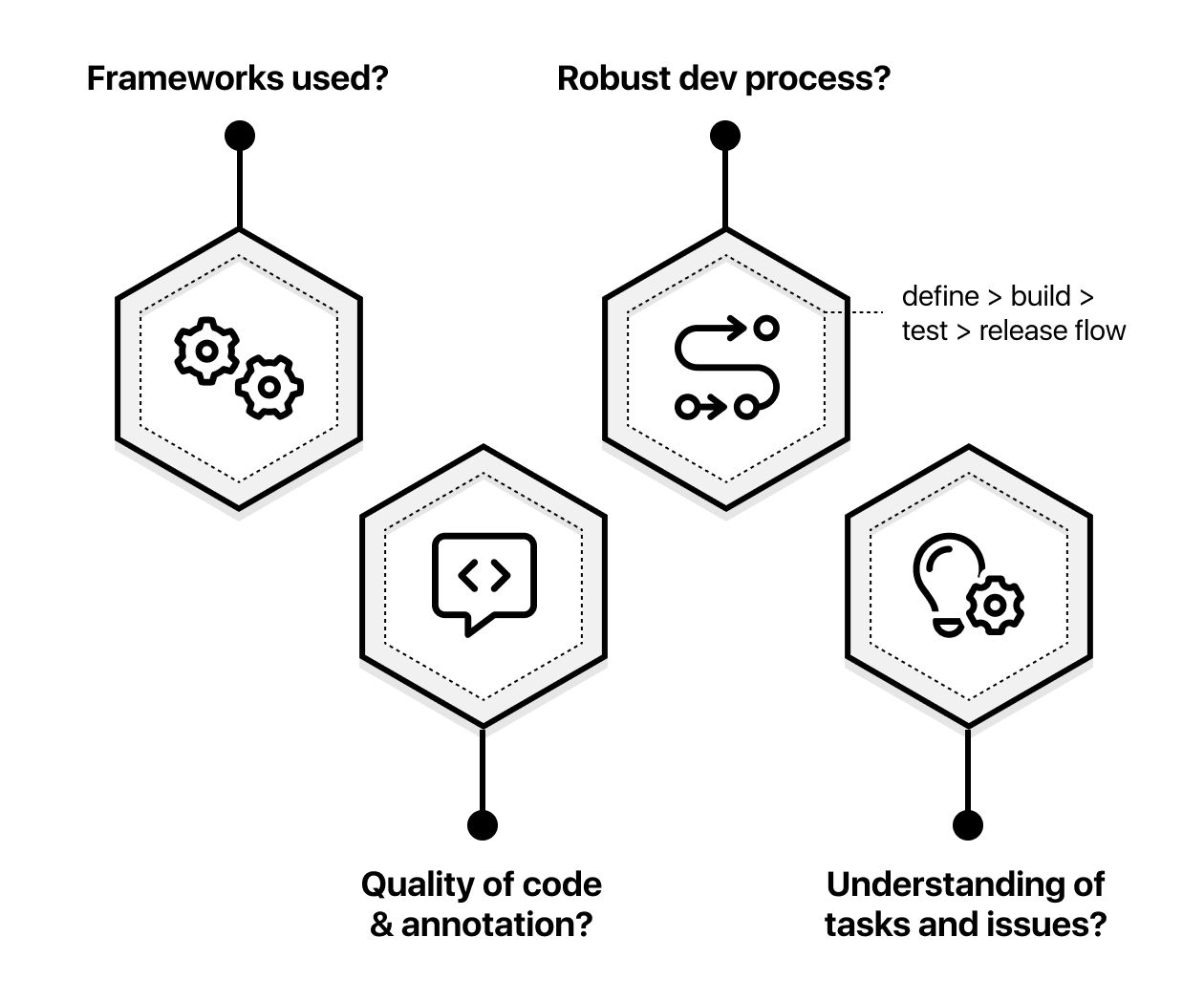
How good is the actual code that runs your site or platform? How well was it developed?
Most software has some level of bugs, but are yours more or less than typical?
Have you picked the right frameworks and tech stack?
Is there unused code in your application which could be exploited?
Are there steps in your process which expose sensitive data?
If a bad actor gains access, what kind of things could they do?
If something does go seriously wrong, can the system be recovered quickly?
We look at your systems from a developer perspective - your team, processes and technology. Unlike the traditional approach, which typically starts from a System Integration and Network view, we start with your code; how it was made, how you test and deploy changes and how you process data.
Even the most bullet proof network and infrastructure can be undone by poor development practices and processes in teams.
Case studies
Cyber Security from a Development perspective
The easiest way to exploit your platform won’t be by dressing up in a Ninja suit and breaking into your network. It will be finding a mistake or loophole in your code, and taking advantage.

How a brand new project can still be insecure
So you've just launched your new project. It must be totally secure right? Not always - there are often vulnerabilities that may reveal over time. Here's how we go looking for them.
Let's build something awesome together
Hire us